Very simple buffer overflow but run in dosbox that emulate MS-DOS. That’s write! This pwnable challenge is 16bit.
|
|
I looked at the list of all functions using Ghidra and I was able to know the main function. Main function address is 0x291.
MS-DOS has not memory protection. So we can run code with any address! But 16bit real address mode use segmentation. We can save we’re shellcode but can’t direct jmp to shellcode address
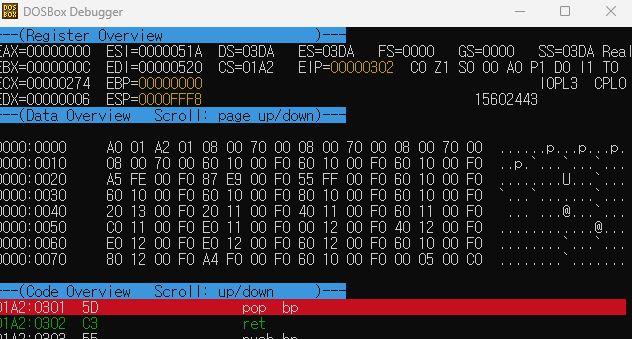
(Debugger shown as 32bit but ignore high 2byte)
Like above picture, SS(Stack Segment) is 0x3DA and CS(Code segment) is 0x1A2. Our shellcode address is SS:0xFFD8 and if we replace ret to 0xFFD8, program jump to CS:0xFFD8 not SS:0xFFD8.
There are a few ways, but I used the retf gadget. RETF (RET FAR) instruction pop cs, ip from stack and jump to CS:IP. RETF gadgget address is placed in 0x91C(abnormal gadget)
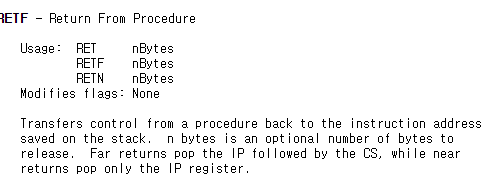
The problem was that the CS and SS addresses when the process started with a debugger were different from the actual environment. To solve this problem, we were able to obtain the address by maximizing the CPU cycle and attaching the debugger.
|
|
|
|
This is my team member’s exploit code. But his idea is exactly same with me.
Shellcode do input.txt to .flag.txt and goto main function. Then main function try to open flag.txt and write flag to OUTPUT.txt
I think this challenge is very interesting. Current operation system dosen’t use segmentation memory management.